CyberFailures Report 2018 Q2
Embrace Failure:
On May 25th 2018 the General Data Protection Regulation came into effect for all organizations globally who provide services (paid or unpaid) for users in Europe. It is a truly global shift in data protection laws. One aspect of the GDPR is mandatory notification of data breacheswhere these users' rights are put at risk.
What if we took these reports, not to see what organizations suffered breaches, but instead to learn valuable lessons from each breach, to raise the bar of cybersecurity across the globe. This is the purpose of the CyberFailures report. We need to embrace the lessons that come from failures, so we can evolve Cyber Security, thereby improving our own organizations and our world.
Bill Gates, the richest man on the planet according to Forbes, once said.
“It's fine to celebrate success but it is more important to heed the lessons of failure.”
― Bill Gates
Create a Culture of Learning:
We need to inject more science into the protection of our data and systems, and to ensure our own well being. The aviation industry has been learning from failures for decades, and we need to bring the same learning technique to Cybersecurity. Incidents from the 1970s still influence some design elements in airliners being built in factories across the world today. Wouldn’t it be great to say the same about Cybersecurity, so that we evolve instead of revolve?
In this report I present findings from the publicly disclosed security incidents of During May (when GDPR came into effect) and June 2018. I intend to publish similar reports on a quarterly basis, depending on your feedback.
Publicly Disclosed Security Incidents May-June 2018
About the data:
I don’t claim this data is a list of all breaches, it is not. I trawled the Web for reported breaches (breaches that were made public in the time period) and dug into each breach as much as possible to determine the cause of the incident. There were 98 breaches in total for May and June 2018. The data published drives the root cause, it may be the case that not all details known were published so there is a margin of error associated with the data. In fact, a number of breach disclosures, even where there were press releases by the organizations involved, did not give enough information to determine the exact cause of the incident. I hope in time that I can build on the data sources, and get increased accuracy, in fact if you work in an organization or CERT and would like to help support this project with more structured anonymous data please get in touch as it will really help reduce the workload in preparing the report.
Incident Descriptions:
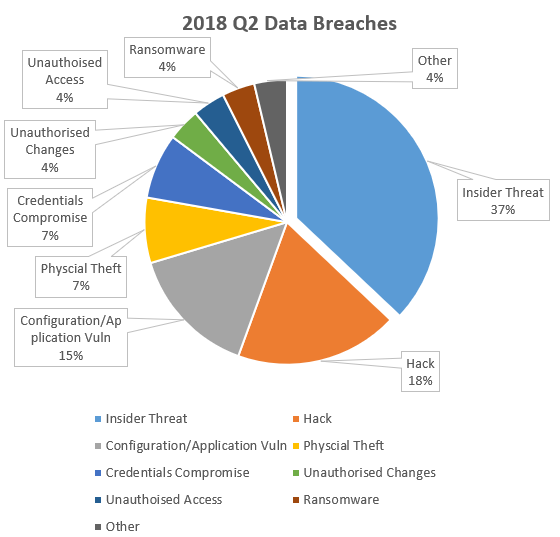
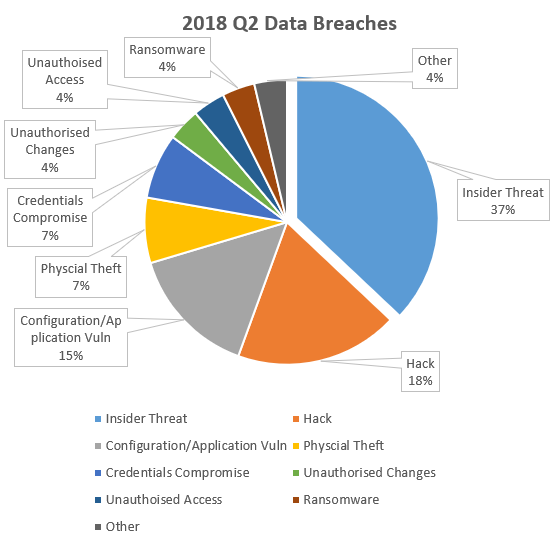
Insider Threats
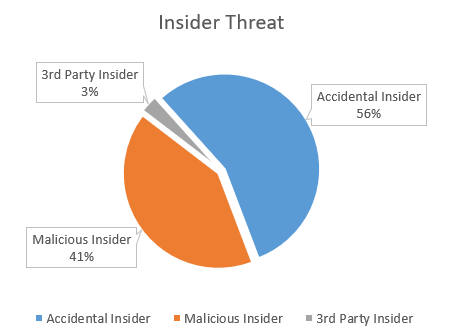
The largest portion of incidents published comes from insider threats. This is an often overlooked threat. This may also explain a recent uptick in viewwers for my Pluralsight course on Insider Threats! We see regular reports of organizations exposing data accidentally by misconfiguring cloud storage such as Amazon’s S3 storage. This has been presented in the data very clearly. We also broke out 3rd parties, who have been given authorized access to systems, and the breach was attributed to such a third party. Again, highlighting the need to ensure security of third party workers and organizations. This is even more important now under GDPR.
Hack
A hack is more generic than I would like, but much of the published statement on breach simply refer to the breach as being the “result of a hack”. The exact cause of the breach is unclear however where there more clear indication of what the hack was, I moved those breaches into the appropriate category from the generic hack category. Largely the hack incidents refer to applications that have been exploited which have been typically in-house developed or hosted applications.
Configuration / Application Vulnerabilities
Configuration and application vulnerabilities refer to off the shelf software that has been misconfigured from a security viewpoint, or has not been hardened enough allowing an attacker to exploit inherent application vulnerabilities. From the information published I have attributed incidents in this category to off-the-shelf products as opposed to bespoke systems.
Physical Theft
This one is obvious, but still important to remind everyone to ensure mobile device and non-mobile device encryption of data is in place. Old style non-Cyber attacks still occur.
Credential Compromise
This is an interesting category. A number of organizations were transparent enough to provide details that the credentials on accounts were compromised. The majority of these were achieved from phishing attacks. The lesson here is to ensure multi-factor authentication is in place for all accounts where possible and use password managers.
Unauthorized Changes
The incidents in this category were driven by malicious attackers. Changes to systems such as web applications to steal payment data and other details, but also making changes to vulnerable web servers for the purpose of SEO ranking manipulation and other attacks.
Unauthorized Access
Several unauthorised access incidents were reported, and not all of these were from some remote rouge nation trying to remotely access data. In fact a notable incident was whereby a hospital noticed unauthorized access to a celebrity's medical and personal information following admission of that celebrity to the emergency department in the hospital. The “attackers” were accessing information for their own curiosity or possibly to share with others. These could have also been categorised as Insider Attacks, but given the poor access control I decided to categories them under this heading.
Ransomware
I must admit the level of reported ransomware incidents surprised me because it was so low. However on reflecting on this, it is more likely that a large scale ransomware incident will get reports, as it is difficult to refute such an attack if it spread to the entire organization. It is also likely that smaller, contained, ransomware attacks never get reported, which might explain the low percentage. I would apply the same rationale to the lack of malware attacks being reported, of course Ransomware is a type of malware, but we have not seen many incidents published where malware was the stated cause.
Other
In a number of incidents there was insufficient information to pinpoint the cause of the incident. The organization involved simply stated there was a breach, but gave no further information. These incidents fall in to the “other” bucket.
Lessons to Learn
As I mentioned at the start of this article, the purpose of reflecting on the incidents that have occurred is to extract learning from them and reduce the likelihood of a similar incident occurring in your organisation.
A great method to learn from these incidents is to prepare a training list that is directly attributable to the incidents that have occurred. This is exactly what I have done here, with the Pluralsight library. Pluralsight have over 6,000 training courses on many topics. Here I focus in on the Security courses, and more particularly the specific courses and content tied to security incidents that have been publicly reported.
Please subscribe to my Pluralsight channel to get a full list of all the courses that are relevant to the incidents reported.
This channel is a curated list from the entire Pluralsight Cybersecurity library, for training content that is directly related to incidents that have been publically reported. So it is not my courses it is all relevant courses, to save you the time of searching through the catalog, you can just jump straight in.
Login to your Pluralsight account and click here for the channel.
If you don’t have a Pluralsight subscription, you can get a free trial here. You should just really subscribe as it is a great resource of learning.
Sectors
I thought about including the sectors where the breaches occured, and to be honest I am still undecided about including this data. My argument against including it is the false comfort that can be taken if you are not in the top industries that have reported breaches. The lessons to be learned from breaches in one industry sector are very transferable to other sectors so I wouldn't want someone looking at the sector list and taking comfort that they don't work in the top sectors reporting breaches and then lower their concern. Another argument against listing the sectors is that some sectors have mandatory reporting requirements such as the HIPPA obligations for the medical sector. So what I have done is simply listed the top three sectors - those sectors that have reported most breaches.
Top 3 sectors:
-
- Medical/Healthcare (most incidents reported)
-
- Government
-
- Education
Other Resources
As I made reference to the airline industry, the investigation work this industry does into incidents in remarkable. Whilst we don't currently have that level of investigative reporting for Cyber security currently here are some helpful resources in to some high profile incidents.
-
GAO report on Equifax Breach
Actions taken by Equifax and Government in response to data breach -
WannaCry impact on UK's National Health Service
UK's National Audit Office Report in to WannaCry Ransomware -
ICO Investigation into Talk Talk Breach
Findings from the investigation into Talk Talk SQL Injection breach
FAQ
Can I reproduce or publish this analysis?
Yes, this work is licensed under a Creative Commons Attribution 4.0 International License. In other words, share generously but provide attribution.
What is the source of data?
I gather the data from the Internet, so anything that is published in relation to a breach. Sometimes organizations publish press releases providing details which is really good. However the majority of data is based on industry reports, with come confirmations from organizations. I have not sought or been given access to any confidential information for the compilation of this report.
Is the analysis perfect and error free?
No it is not error free, absolutely not, but it is a start, and I have not been able to find actionable reports anywhere else, so by publishing this report with directly related training content on Pluralsight, the learning is immediately actionable if you have a Pluralsight subscription. If you don’t sign up for a free trial, or just subscribe, it is a great resource !
How do I contact you?
You can reach me via multiple channels, see my contact page if you want to discuss anything in relation to this report.
Why publish this information?
I want to see organizations learn from experiences and incidents experienced by every other organization globally, this is the only way we will raise the bar for Cybersecurity.